The Combined Power of Identity & Access Management and Data Access Controls
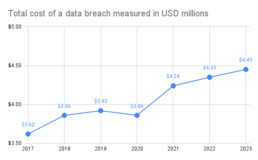
The digital age presents a double-edged sword for businesses. While technology advancements offer exciting capabilities in cloud, data analytics, and customer experience, they also introduce new security challenges. Data breaches are a constant threat, costing businesses an average of $4.45 million per incident according to a 2023 IBM report (https://www.ibm.com/reports/data-breach) and eroding consumer trust. Traditional security measures often fall short, leaving vulnerabilities for attackers to exploit. These attackers, targeting poorly managed identities and weak data protection, aim to disrupt operations, steal sensitive information, or even hold companies hostage. The impact extends beyond the business itself, damaging customers, stakeholders, and the broader financial market
In response to these evolving threats, the European Commission (EU) has implemented the Digital Operational Resilience Act (DORA) (Regulation (EU) 2022/2554). This regulation focuses on strengthening information and communications technology (ICT) resilience standards in the financial services sector. While designed for the EU, DORA’s requirements offer valuable insights for businesses globally, especially those with operations in the EU or the UK. DORA mandates that financial institutions define, approve, oversee, and be accountable for implementing a robust risk-management framework. This is where identity & access management (IAM) and data access controls (DAC).
The Threat Landscape and Importance of Data Security
Data breaches are just one piece of the security puzzle. Malicious entities also employ malware, phishing attacks, and even exploit human error to gain unauthorised access to sensitive data. Regulatory compliance further emphasises the importance of data security. Frameworks like GDPR and HIPAA mandate robust data protection measures. Failure to comply can result in hefty fines and reputational damage.
Organisations, in a rapidly-evolving hybrid working environment, urgently need to implement or review their information security strategy. This includes solutions that not only reduce the attack surface but also improve control over who accesses what data within the organisation. IAM and DAC, along with fine-grained access provisioning for various data formats, are critical components of a strong cybersecurity strategy.
Keep reading to learn the key differences between IAM and DAC, and how they work in tandem to create a strong security posture.
Identity & Access Management (IAM)
Think of IAM as the gatekeeper to your digital environment. It ensures only authorised users can access specific systems and resources. Here is a breakdown of its core components:
- Identity Management (authentication): This involves creating, managing, and authenticating user identities. IAM systems manage user provisioning (granting access), authentication (verifying user identity through methods like passwords or multi-factor authentication [MFA]), and authorisation (determining user permissions). Common identity management practices include:
- Single Sign-On (SSO): Users can access multiple applications with a single login, improving convenience and security.
- Multi-Factor Authentication (MFA):An extra layer of security requiring an additional verification factor beyond a password (e.g., fingerprint, security code).
- Passwordless: A recent usability improvement removes the use of passwords and replaces them with authentication apps and biometrics.
- Adaptive or Risk-based Authentication: Uses AI and machine learning to analyse user behaviour and adjust authentication requirements in real-time based on risk level.
- Access Management (authorisation): Once a user has had their identity authenticated, then access management checks to see what resources the user has access to. IAM systems apply tailored access policies based on user identities and other attributes. Once verified, IAM controls access to applications, data, and other resources.
Advanced IAM concepts like Privileged Access Management (PAM) focus on securing access for privileged users with high-level permissions, while Identity Governance ensures user access is reviewed and updated regularly.
Data Access Control (DAC)
While IAM focuses on user identities and overall system access, DAC takes a more granular approach, regulating access to specific data stored within those systems. Here are some common DAC models:
- Discretionary Access Control (also DAC): Allows data owners to manage access permissions for other users. While offering flexibility, it can lead to inconsistencies and security risks if not managed properly. One example of this is UNIX files, where an owner of a file can grant or deny other users access.
- Mandatory Access Control (MAC): Here, the system enforces access based on pre-defined security labels assigned to data and users. This offers stricter control but requires careful configuration.
- Role-Based Access Control (RBAC): This approach complements IAM RBAC by defining access permissions for specific data sets based on user roles.
- Attribute-Based Access Control (ABAC): Permissions are granted based on a combination of user attributes, data attributes, and environmental attributes, offering a more dynamic and contextual approach.
- Encryption: Data is rendered unreadable without the appropriate decryption key, adding another layer of protection.
IAM vs. DAC: Key Differences and Working Together
While IAM and DAC serve distinct purposes, they work in harmony to create a comprehensive security posture. Here is a table summarising the key differences:
FEATURE
IAM
DAC
Description
Controls access to applications
Controls access to data within applications
Granularity
Broader – manages access to entire systems
More fine-grained – controls access to specific data check user attributes
Enforcement
User-based (IAM) or system-based (MAC)
System-based enforcement (MAC) or user-based (DAC)
Imagine an employee accessing customer data in a CRM system. IAM verifies their identity and grants access to the CRM application. However, DAC determines what specific customer data they can view or modify based on their role (e.g., a sales representative might have access to contact information but not financial details).
Dispelling Common Myths
Several misconceptions surround IAM and DAC. Here is why they are not entirely accurate:
- Myth 1: IAM is all I need. The most common mistake that organisations make is to conflate IAM and DAC, or worse, assume that if they have IAM, that includes DAC. Here is a hint. It does not.
- Myth 2: IAM is only needed by large enterprises. Businesses of all sizes must use IAM to secure access to their applications and ensure compliance. Scalable IAM solutions are readily available.
- Myth 3: More IAM tools equal better security. A layered approach is crucial. Implementing too many overlapping IAM tools can create complexity and management overhead. Focus on choosing the right tools that complement each other and address specific security needs.
- Myth 4: Data access control is enough for complete security. While DAC plays a vital role, it is only one piece of the puzzle. Strong IAM practices ensure authorised users are accessing systems, while DAC manages their access to specific data within those systems. A comprehensive security strategy requires both.
Tools for Effective IAM and DAC
There are various IAM and DAC solutions available, and the best choice depends on your specific needs. While Active Directory remains a popular IAM solution for Windows-based environments, it may not be ideal for complex IT infrastructures or organisations managing vast numbers of users and data access needs.
Imagine a scenario where your application has 1,000 users and holds sensitive & personal customer information for 1,000,000 customers split across ten countries and five products. Not every user should see every customer record. It might be limited to the country the user works in and the specific product they support. This is the “Principle of Least Privilege.” Applying this principle is critical to demonstrating you have appropriate data access controls.
To control access to this data, you would need to create tens of thousands of AD groups for every combination of country or countries and product or products. This is unsustainable and makes choosing AD groups to manage data access control an extremely poor choice.
The complexity of managing nested AD groups and potential integration challenges with non-Windows systems highlight the importance of carefully evaluating your specific needs when choosing IAM tools. Consider exploring cloud-based IAM platforms or Identity Governance and Administration (IGA) solutions for centralised management and streamlined access control.
Building a Strong Security Strategy
The EU’s Digital Operational Resilience Act (DORA) emphasises strong IAM practices for financial institutions and will coming into act from 17 January 2025. DORA requires financial organisations to define, approve, oversee, and be accountable for implementing robust IAM and data access controls as part of their risk management framework.
Here are some key areas where IAM and DAC can help organisations comply with DORA and protect themselves:
DORA Pillar
How IAM helps
How DAC helps
ICT risk management
- Identifies risks associated with unauthorised access/misuse
- Detects users with excessive permissions or dormant accounts
- Minimises damage from breaches by restricting access to specific data
ICT related incident reporting
- Provides audit logs for investigating breaches (user activity, login attempts, accessed resources)
- Helps identify source of attack and compromised accounts
- Helps determine scope of breach and potentially affected information
ICT third-party risk management
- Manages access for third-party vendors/partners
- Grants temporary access with limited permissions, reducing attack surface
- Restricts access for third-party vendors by limiting ability to view/modify sensitive data
Information sharing
- Permissions designated users authorised to share sensitive information
- Controls access to shared information via roles and rules
Digital operational resilience testing
- Enables testing of IAM controls to identify vulnerabilities
- Penetration testing simulates attacks to assess effectiveness of IAM controls
- Ensures data access restrictions are properly enforced and minimizes breach impact
Understanding IAM and DAC empowers you to build a robust data security strategy
Use these strategies to leverage the benefits of IAM and DAC combined:
- Recognise the difference between IAM and DAC, and how they are implemented in your organisation
- Conduct regular IAM and DAC audits to identify and address vulnerabilities
- Implement best practices like the Principle of Least Privilege (granting users only the minimum access required for their job function)
- Regularly review and update user access permissions
- Educate employees on security best practices (e.g., password hygiene, phishing awareness)
Explore different IAM and DAC solutions based on your specific organisational needs and security posture. Remember, a layered approach that combines IAM, DAC, and other security measures like encryption creates the most effective defence against data breaches and unauthorised access.
Conclusion
By leveraging the combined power of IAM and DAC, you can ensure only the right people have access to the right data at the right time. This fosters trust with stakeholders, protects your reputation, and safeguards your valuable information assets.